Understanding the Man-in-the-Middle Attacks
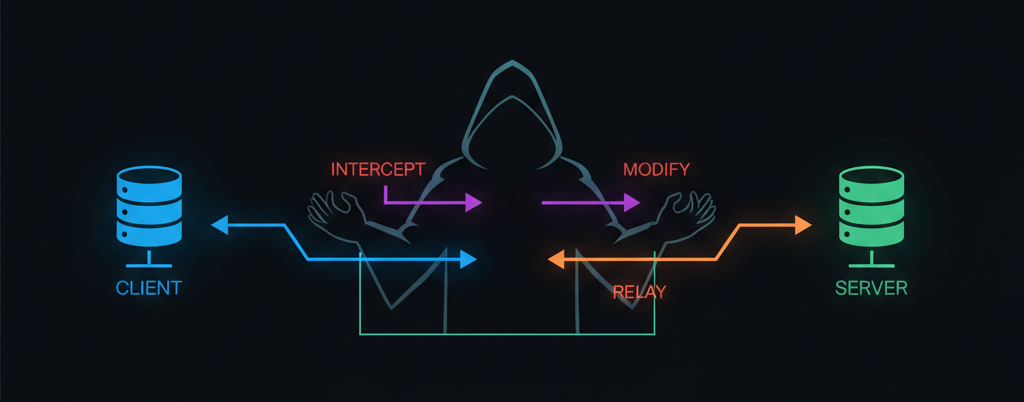
The Invisible Eavesdropper
Imagine sitting in a café, having a private conversation with someone you trust. You believe it’s just the two of you, but a stranger nearby is quietly listening, catching every word. Now, apply that same concept to the internet. You think your device is communicating securely with a website or app, but someone in between might be intercepting, recording, or even altering the exchange without your knowledge.
That’s the essence of a Man-in-the-Middle (MitM) attack — when a malicious third party secretly positions itself between your device and the system you’re trying to reach. The attacker can read, modify, or impersonate communications, all while everything appears perfectly normal to the user.
How MitM Attacks Work
In many cases, the attacker doesn’t need to install malware or steal passwords. Instead, they exploit weaknesses in how data travels across networks especially unsecured or misconfigured ones. These attacks are silent, fast, and surprisingly common
Public Wi-Fi: The Perfect Hunting Ground
One of the most frequent scenarios for MitM attacks is public Wi-Fi. When you connect to free Wi-Fi at coffee shops, airports, or hotels, your data often moves across the network unencrypted. If an attacker is connected to the same network, they can use sniffing tools to monitor and capture traffic in real time — exposing login credentials, banking details, and even emails.
Another common trick is setting up fake Wi-Fi access points that look legitimate, often using the same name as a nearby business. Once you connect, every click, message, or file passes through a system controlled by the attacker.
DNS Spoofing and HTTPS Stripping
Some MitM attacks use more technical deception. In DNS spoofing, the attacker redirects you to a fake version of a trusted website. The site looks identical to the real one, but anything you enter usernames, passwords, or card details, goes straight to the attacker. Because the browser still shows the correct URL, most users never notice.
HTTPS stripping is another subtle trick. When a site supports both secure (HTTPS) and insecure (HTTP) connections, the attacker intercepts your initial request and forces you onto the unencrypted version. This removes encryption, allowing the attacker to view and manipulate all traffic in plain text.
Session Hijacking and Sniffing
Once you log into a website, your identity is maintained through a session token or cookie. If an attacker captures that information, they can hijack your session and impersonate you without ever needing your password.
Sniffing involves monitoring and capturing unencrypted network traffic. Attackers can see visited sites, entered text, and even uploaded files. A low-tech variant, shoulder surfing, happens when someone physically watches you enter passwords or view sensitive data in public spaces.
The Real-World Consequences
The fallout from MitM attacks varies with what’s captured. Cybercriminals may steal login credentials, intercept financial transactions, or access confidential communications. In a corporate setting, attackers can inject malicious payloads, redirect payments, or penetrate internal systems leading to serious financial and reputational damage.
Defending Against MitM Attacks
Despite their sophistication, MitM attacks can often be prevented through awareness and consistent habits.
Avoid public Wi-Fi for sensitive activities such as banking or work logins.
If you must connect, use a trusted VPN to encrypt your traffic.
Always ensure websites use HTTPS and display a valid security certificate.
Keep devices and applications updated to patch vulnerabilities.
Be skeptical of pop-ups, login prompts, or websites that look slightly off.
Enable two-factor authentication (2FA) wherever possible.
In public, remain mindful of your surroundings. Use privacy screen filters, and never leave devices unlocked or unattended.
Awareness Is the Strongest Shield
Man-in-the-Middle attacks exploit the invisible trust we place in our daily digital connections. They rarely leave visible traces, making prevention far more effective than detection. By understanding how these attacks work — and practicing good security hygiene — individuals and organizations can greatly reduce their exposure.
Vigilance and awareness remain the most reliable defenses against invisible threats like these.
